Yara is mostly recognized as a tool to detect, identify and classify malware samples. In general it allows you to identify any binary or textual pattern, such as hexadecimal and strings contained within a file. If you started your journey, as a SOC member, sooner or later you will need to know how Yara rules works, and how they can help you in every day duties. Especially when you want to develop your skills in malware analysis or reverse engineering.

Yara rules are written, to label patterns and based on labels, determine if file is malicious or not.
Strings are the fundamentals of programming because applications store data as a strings. Simplest example of how the string is stored is code written in Python.
Create a file called helloworld.py and add a code there.
1 | print("Hello world!") |
If you do not have python installed (shame on you - just kidding). You can use online python compiler or make this exercises on Kali Linux or Parrot OS.
If you run the code python helloworld.py it will just display text string Hello world!. Easy peasy. Malware is just an application, but malicious. Also uses strings to store textual data. It can be a Bitcoin wallet address, process name, path, IP address etc. Just a string of data which is characteristic. Thanks to Yara we can write a rule which will find strings in all applications in our operating system.
Install, create and run Yara
Lets install Yara and write some rules, to understand how it works. Yara is multiplatform application, so you can just download it and install in Windows or using Linux (eg. Kali) type in terminal:
1 | sudo apt install yara |
Running Yara is simple, command requires two arguments, first is the rule file and second the name of file, directory, or process ID to use the rule for.
Every rule must have a name and condition.
So for example if we want to run rule.yar on user directory in Linux we need to run:
1 | yara rule.yar /home/user |
Like you can see the extension for Yara files is .yar Lets create now basic rule.
1 | touch myfirstrule.yar |
edit it using your favorite text editor:
1 | nano myfirstrule.yar |
and put there:
1 | rule helloworld_checker { |
Rule name in this case is helloworld_checker, keyword we want to search for, is a string Hello world! and condition is variable $hello_world (so the string Hello world!). We satisfied two main Yara requirements (name and condition).
In this case our Yara rule will find any file that has the string Hello world!. Keywords are case sensitive so we can tweak our rule.
1 | rule helloworld_checker { |
We modify also condition to match all keywords. Now these strings will trigger the rule, Hello world!, hello world, HELLO WORLD.
Conditions
More details and conditions can be found in docs. Here are some examples:
File size
Size of the file being scanned
1 | rule FileSizeExample |
Counting
How many times the string appears in the file.
1 | rule CountExample |
Test it
Do you remember the file we created earlier helloworld.py. Run your myfirstrule.yar on that file and check if it works.
1 | yara myfirstrule.yar helloworld.py |
the output should looks like:
1 | helloworld_checker helloworld.py |
What happened, how to read the output? File called helloworld.py was labeled as helloworld_checker (name of rule). Create few more various files in same location, with different content, and put to one of them string HELLO WORLD. Run your Yara rule on folder with all files.
1 | yara myfirstrule.yar /home/user/test_folder/ |
Now you should see two files labeled as helloworld_checker. This simple example shows how it works, and how this rule detects files.
Here you can find nice cheatsheet for Yara rules created by Thomas Roccia.
Examples above are easy, unfortunately building complex Yara rules are not so easy. Fortunately you do not have to write them, because there are so many already, you can download them and just use. Check this Awesome Yara GitHub repository for more rules and tools.
The tools
Here are few tool worth mention.
Loki
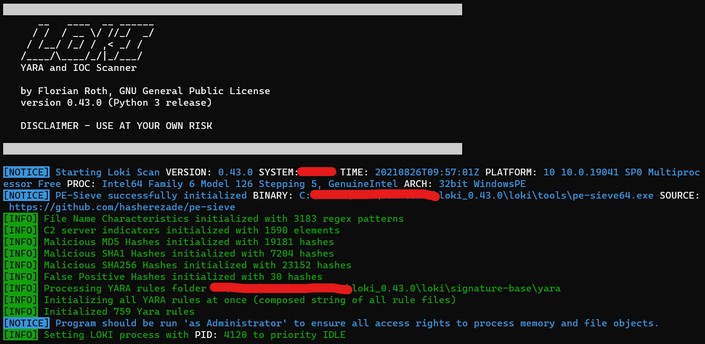
LOKI is a free open source IOC (Indicator of Compromise) scanner created/written by Florian Roth.
Detection is based on 4 methods (File Name IOC Check, Yara Rule Check, Hash Check, C2 Back Connect Check).
Run it:
1 | ./loki.py -p /path_to_scan/ --onlyrelevant -l /tmp/loki_logs.txt |
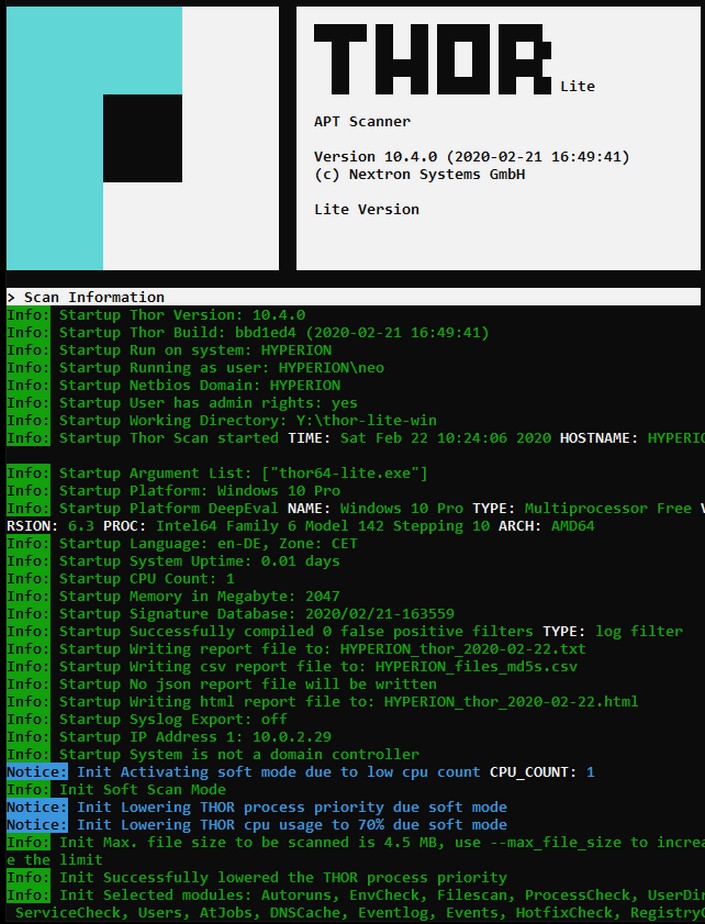
Thor Lite
New fast and flexible multi-platform IOC and YARA scanner THOR in a reduced free version named THOR Lite. THOR Lite includes the file system and process scan module as well as module that extracts “autoruns” information on the different platforms. While enterprise scanner THOR uses VALHALLA‘s big YARA rule base, the free THOR Lite version ships with the Open Source signature base, which is also part of our free Python scanner LOKI.
YAYA
YAYA is a new open source tool to help researchers manage multiple YARA rule repositories. YAYA starts by importing a set of high-quality YARA rules and then lets researchers add their own rules, disable specific rulesets, and run scans of files.
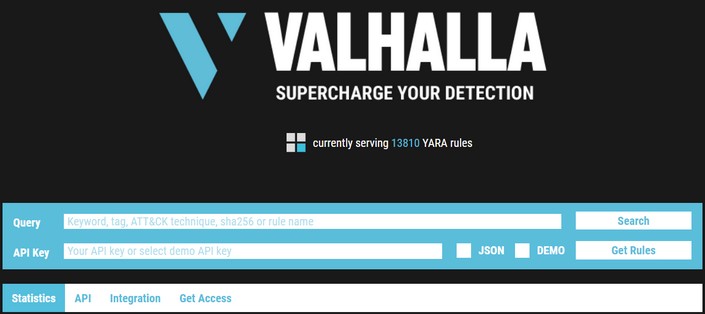
Valhalla
Valhalla is an online Yara feed created and hosted by Nextron-Systems. You can conduct searches based on a keyword, tag, ATT&CK technique, sha256, or rule name
yarGen
yarGen is a generator for YARA rules. The main principle is the creation of yara rules from strings found in malware files while removing all strings that also appear in goodware files. Therefore yarGen includes a big goodware strings and opcode database as ZIP archives that have to be extracted before the first use.
Before generate any yar files update yarGen:
1 | python3 yarGen.py --update |
If you have malicious file and want to find other similar suspicious files based on it, you can create yara rule from that file.
1 | python3 yarGen.py -m /home/user/new_suspicious_file --excludegood -o /home/user/new_suspicious_file.yar |
-m is the path to the files you want to generate rules for--excludegood force to exclude all goodware strings (these are strings found in legitimate software and can increase false positives)-o location & name you want to output the Yara rule
Always open generated rule and review it, remove things might generate false positives.
yarAnalyzer
When you generate yara rule using yarGen, you might to analyze results, manually it can be painful, so to automate this process you can use yarAnalyzer - Yara Rule Analyzer and Statistics.
1 | yarAnalyzer.py -p /sample/path -s /signatures |
More materials
After that small introduction you might be hungry for Yara knowledge.
Go and check these materials to learn more!
How to Write Simple but Sound Yara Rules - Part 1